CTI Indicators : Human Risk integration - ANOZR WAY Partnership
The Security Incident category has been enhanced with new CTI indicators through the partnership with ANOZR WAY.
What is Cyber Human Risk?
Human cyber risk encompasses all behaviors, actions, or omissions—whether intentional or unintentional—that could compromise the cybersecurity of an organization or an individual.
Today, human vulnerabilities are the main entry point for cybercriminals. They exploit the large amount of publicly accessible or stolen information to refine their attack scenarios: social engineering, phishing, identity theft, account compromise, fraud, etc. For them, exposed personal data is a goldmine. Public profiles, uncontrolled digital footprints, and correlations between professional identifiers and personal usage together create an expanded attack surface, often poorly addressed by traditional technical cybersecurity approaches.
In general, human cyber risk tends to increase under the influence of several factors:
- The growing volume of personal data that can be exploited by hackers, driven by the massive and ever-expanding use of social networks
- Large-scale attacks on public and private organizations aimed at collecting users’ critical personal data
- The rise of remote work and the blurring of boundaries between professional and personal life
- The advancement of OSINT (Open-Source Intelligence) techniques used by attackers
- The automation and industrialization of social engineering attacks (e.g., personalized phishing/smishing, identity and account theft)
- The increasing sophistication of Deepfake technologies.
What is the methodology used to calculate the risk level?
The risk level is a weighted sum of various threat indicators. For exemple, a leak from an infostealer would have more impact than a professional email leak. These indicators are calculated based on information found on the dark web, making the threat probable. The weights of the different indicators have been calibrated based on the measurement of risk for over 10,000 domain names.
Which assets is the assessment based on to determine the human risk? Could domain names be added?
The assessment is based on mail domains (at firest level and not subdomains, used for messaging that contain a DNS record of type MX) included in the scope of your global asset mapping. We invite you to check that these domains are correctly listed for this purpose, and if necessary, to add them (here is an article to help you with this).
How does the score change over time?
The risk indicators related to data breaches have a validity period of 6 months. If a domain name no longer experiences data breaches for 6 months, its score decreases to 0. Leaks older than six months no longer affect the score. For ransomware, the impact on the score decreases according to a decreasing exponential. The impact on the score can have an effect of up to 10% on the overall grade.
How to improve the Rating?
The score increases gradually over time (evaluation window of 6 months). For example, if a data breach was detected on 01/01/2025, then around 06/01/2025, i.e. 6 months later, there will be no further impact and the score will increase. It is also important to note that the CTI score is refreshed on a weekly basis.
Moreover, in future developments of this analysis axis, we plan to take into account the remediations handled with ANOZR WAY solutions (as a client) in the evolution of the score.
What are the sources?
The CTI reports come from OSINT (Open-Source Intelligence) and data available on darknet forums. They are verified by Anozr Way's expertise to avoid false positives. The sample available on the platform allows you to legitimize the shared data. We enable you to verify it on your own domain.
Which regulatory Framework applies to this sssessment?
To be lawful, the processing of personal data must be based on a "legal basis" provided by the GDPR. There are six legal bases in total, and we rely on the legitimate interest basis, which allows us to process these data. In other words, there is a legitimate interest (in this case, a cybersecurity necessity) that authorizes the processing of personal data. European institutions and the CNIL explain that cybersecurity-related processing is based on this legitimate interest basis.
How to access the sample?
Any Sponsor user of the account (restricted to companies or not) or Audited administrator of the company, with an email address similar to the analyzed domain name, can access the sampling to verify the legitimacy of the data.
To access it, simply click on the domain name in question and then on "Get a sample":
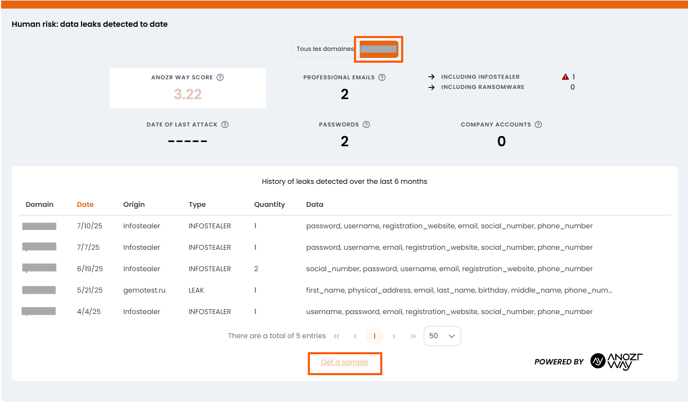
What does the sample correspond to?
The proposed sample of data (maximum 5) on each messaging domain is provided in order to give you context and legitimize the information we provide you in the form of CTI indicators. It is provided only for leaks of passwords and/or emails. This data is particularly important due to its secret nature.
Board of Cyber’s mission is to deliver clear, reliable and understandable indicators about your external position, emphasizing simplicity and readability rather than exhaustive details or long-term retention of this type of data. This specialized service is delivered by our partner Anozr Way. As a result, the Security Rating platform displays a partially anonymized representation through those samples.
What would be the added value to contractualized with Anozr Way ?
The human risk rating integrated into Security Rating provides initial visibility, but it remains focused on a restricted set of attack scenarios (account and identity theft). This approach, although relevant, does not reflect the entire range of threats to which employees and executives are exposed. ANOZR WAY solutions complement and enrich this vision by covering a much broader spectrum of cyber risks, including targeted phishing, SIM swapping, smishing, and other forms of attacks exploiting human vulnerability.
Another major difference: Security Rating does not integrate the personal dimension of digital exposure, whereas this is a frequent entry point for cybercriminals. ANOZR WAY goes further by rebounding from professional data to personal information, revealing invisible vulnerabilities in an analysis limited to the professional perimeter.
Finally, ANOZR WAY is not limited to evaluation. The solution provides concrete and personalized action plans to remediate and reduce individual exposure and risk level over time. While Security Rating provides a snapshot at a given time, ANOZR WAY offers a dynamic protection and active reduction of human risk.
For more information, visit the ANOZR WAY website.![BoardofCyber_Logo_Blanc.png]](https://content.boardofcyber.io/hs-fs/hubfs/Dossier%20partenaires%20FR/BoardofCyber_Logo_Blanc.png?height=50&name=BoardofCyber_Logo_Blanc.png)